No matter if it’s private communication or business, your emails contain practically all the information there is to know about you and your business

From your emails, anyone can learn about your work, our relationships, our vacations, and our medical problems. Someone in control of your email account could impersonate you and scam your friends and business partners, as well as reset passwords to any account linked to the email address.
Email security is of high importance, and while perfect anonymity and security might seem unachievable, it is rather easy to secure your account against some of the most equipped adversaries — and without too much cost.
Strong passwords protect your account from hacking
To make sure that no one else has access to your account, simply change your password. The most important characteristic of your password is that it should be unique. This means not only do you not use this password on any other service, nobody uses this password on any service.
Ideally, your password is also a long one. A password manager and the diceware technique can both help you to find a good unique password.
You should also enable two-factor authentication for your email account. Two-factor authentication works by sending a secondary, one-time password by text message to a registered phone, making it far harder for anybody to access your account, even if they have your password.
Regular housekeeping on your account is essential for good security. Make sure that no one has set any redirects or filters that automatically forward your email to another account.
Also, check your previous logins and see if you find anything suspicious. Some email providers allow you to link your account to other apps or platforms. Make sure that all of these integrations are trustworthy and needed.
Don’t load images and be careful about tracking links
To track the reach and effectiveness of their emails, many companies, especially newsletter providers, will track the links in their emails. This is done to see how many people, and even who exactly, read the email, clicked on certain links, or forwarded the email.
When you hover your mouse over a link, your browser should show you its destination, which you can copy it into a text editor for further inspection. You could open the link in the Tor Browser to disguise your location, although this would still reveal the time you opened the link.
Another strategy used to track you is to include images into your emails. When you open the email, you automatically load the image from a remote server. This can contain a tracking code, and reveal to mailing list administrators who opened the message. You can most likely configure your email provider to not load external images by default, thus disabling the tracking code.
Links might not only track you, but rather send you to sites that host malware, or phishing sites.
Be careful opening attachments
Attachments can contain all kinds of malware, such as cryptolockers or trojans. Only click on files that you expect, and whose senders you trust.
It is advisable to open commonly infected formats such as pdf, xls, and doc using the built-in functionality of your webmail provider, or to open them in a virtual machine. Either way, make sure your computer is up to date. Antivirus software helps but is not a guarantee of a virus-free computer.
Always use TLS
TLS stands for Transport Layer Security, and it ensures your connection to a website is encrypted as well as verifying the integrity of the server you are connecting to. TLS is also used to encrypt your connection to an email server and connections between email servers.
When you use an external email client, such as Outlook, Apple Mail, or Thunderbird, always make sure your emails are fetched over an encrypted channel.
Go into your settings and ensure “STARTTLS” or “SSL/TLS” is activated.
- Some software may call this connect only through encrypted channels
TLS ensures that emails are encrypted between your computer and the email server, so they cannot be easily intercepted.
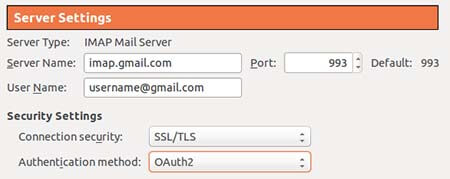
It is important to encrypt emails not only between your computer and your email server but also between email servers.
This is also done with TLS. You can use the tool CheckTLS to see if your email server encrypts between servers.
Simply enter your email address (or that of anyone else) into CheckTLS.
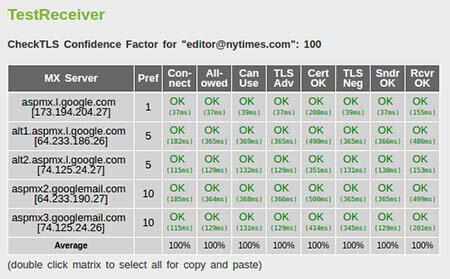
Your test results should look like this. Everything is green, indicating all emails are encrypted when sent between servers, and the certificates are valid.
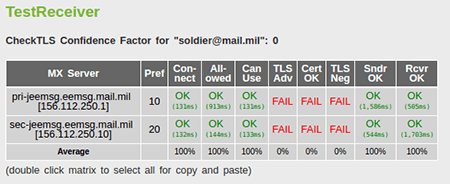
If you see a red Fail under TLS, you need to urge your email provider to configure their servers correctly, or switch providers. (Yes, the U.S. Military does not encrypt its email!)
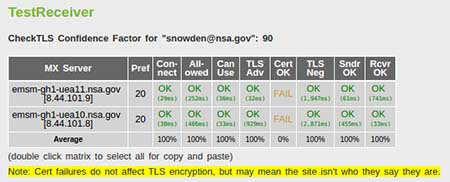
In many cases, you will see a result like the one above. The Cert OK fail indicates that while the nsa.gov email servers do use encryption, they do not have a valid certificate, making them vulnerable to man-in-the-middle attacks. If you encounter this problem, reach out to your email provider, system administrator, or look out for a new one.
Encrypt your emails with PGP
It is possible to encrypt emails to protect them from being snooped on, intercepted, and altered by even the most skilled and well-funded adversaries.
Pretty Good Privacy (PGP), also called GNU Privacy Guard (GPG), is free software that encrypts the contents of your email in a way that means only the intended recipient can see it. However, it does require the recipient to use the software as well.
When using PGP, both you and your contacts will create a keypair on your devices, which includes a public and a private part. You can exchange the public key, verify its authenticity, and encrypt your emails with this key. To decrypt the information the private key is necessary, which never leaves the computer.
Though very secure, PGP does still leave some information out in the open, called metadata. The metadata includes the email addresses of the sender, recipient, time the message was sent, and the approximate email size.
Avoiding metadata is difficult and might entail not using emails at all. For an example, have a look at Off-the-record (OTR) , an encrypted chat protocol. OTR encrypts your messages, but also creates a new key for each conversation, to make it more difficult to link them.
This article teaches you how to set up an anonymous jabber account, enable OTR encryption, and route your chats through the Tor network.




